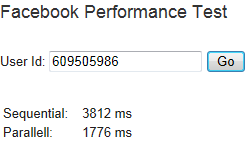
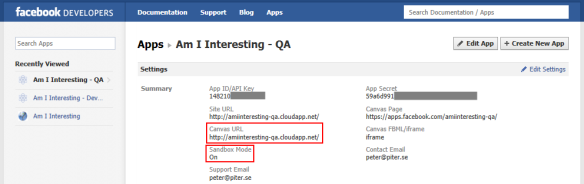
On top of the ASP.NET MVC web app for Am I Interesting (AII), I’m also adding a Windows Phone 7 client application. This application needs to first authenticate against Facebook and retrieve a Facebook access token before passing that token when authenticating against the API for AII.
This is a two-part blog post:
Part 1 – Configuring ACS for Facebook Authentication
Part 2 – Implementing ACS in your WP7 app (next post)
For this authentication, I will use Azure AppFabric Access Control Service (ACS) from the WP7 app. ACS offers a convenient way to authenticate against identity providers such as Windows Live, Facebook, Google and Yahoo, and it’s priced at only $1.99 per 100,000 transactions. If you, like me, have an MSDN subscription, you also have 100,000-500,000 transactions per month included free of charge.
To set up ACS, go to the Windows Azure Management Portal, navigate to “Service Bus, Access Control & Caching” and click to create a new service namespace:
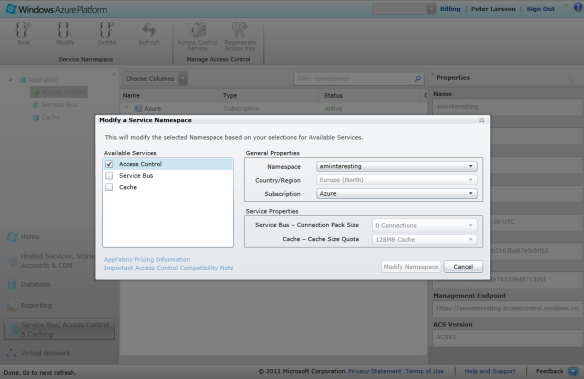
Check the Access Control check box and enter a unique namespace, “amiinteresting” in my case.
The next step is to add Facebook as an identity provider to your created service namespace. Click to manage Access Control Service:

Click on Identity providers and then Add:

Enter a display name, your Facebook Application Id and Facebook Application Secret (from the Facebook developer portal), and a comma-separated list of Application permissions that you need. Offline_access is needed if you don’t want your WP7 users to have to enter their login credentials every time they start the app:
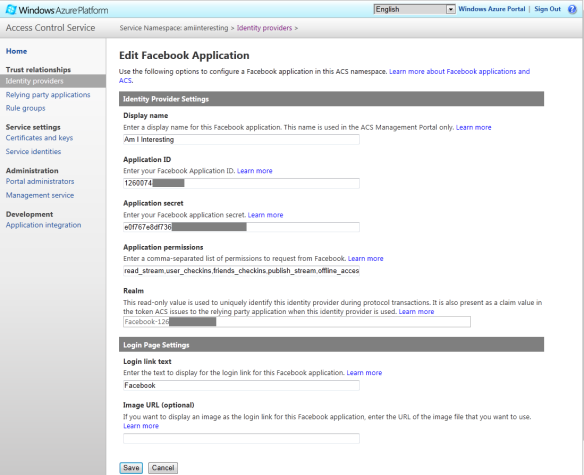
I have added two Identity providers for the two different Facebook applications I use for Development (local debugging) and Production with different Application Ids and Application Secrets.
The next step is to tell ACS about the client application (relying party) that will connect to ACS to authenticate users. To do this, navigate to Relying party applications and click on Add:

For a thick client application, that will not use browser redirection, it’s enough to enter a display Name, a URI Realm that the token should be issued for (a bit tricky subject, described here), which in my case is the application URI https://www.amiinteresting.net, and a Token format. I have chosen a Simple Web Token (SWT) which is suitable for tokens that are be passed in the HTTP header or request, which is normally the case when communicating with REST (or REST-alike) API:s:
Further down on the page, choose the Identity provider that was added in a previous step and click to Generate a token signing key for this relying party application:
The last thing you need to do is configure the Rule group that was automatically created when you added the relying party. A rule group is used to define how claims from the identity provider (Facebook) are passed to the relying party (WP7 app). Navigate to Rule groups and click on the automatically added rule group to configure:
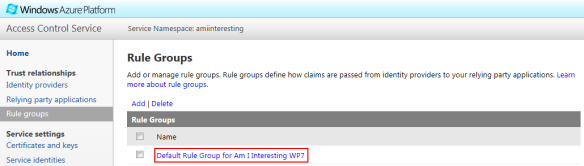
On the screen that appears, no rules will have been added yet. The rules can be added individually/manually, or you can click on Generate to automatically generate rules for you:
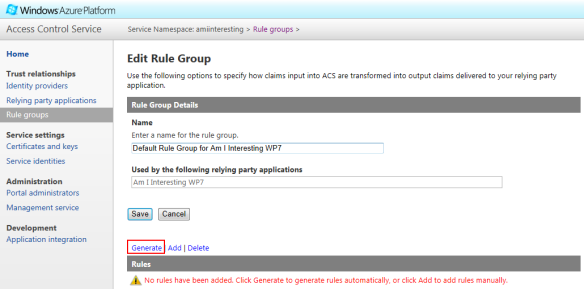
On the next screen, I have chosen to generate rules for both my Facebook applications (development and production):

I then modified the generated rules by removing the emailaddress claim (I don’t need and therefore didn’t configure the Identity provider to request the email permission from Facebook) and changing the description of the nameidentifier claim to “Facebook User Id” (which it is):

Done! ACS is now configured for Facebook authentication and ready to be used by WP7!
Stay tuned for the next post that covers how to connect the WP7 app to ACS and ultimately get the Facebook access token, which is required to authenticate against the API for Am I Interesting….
![]()